[Reverse Engineering] by DarkEnigma
Challenge 1: [basic] reverse engineering (50 pts)
Solution: just find a flag in strings window 🙂
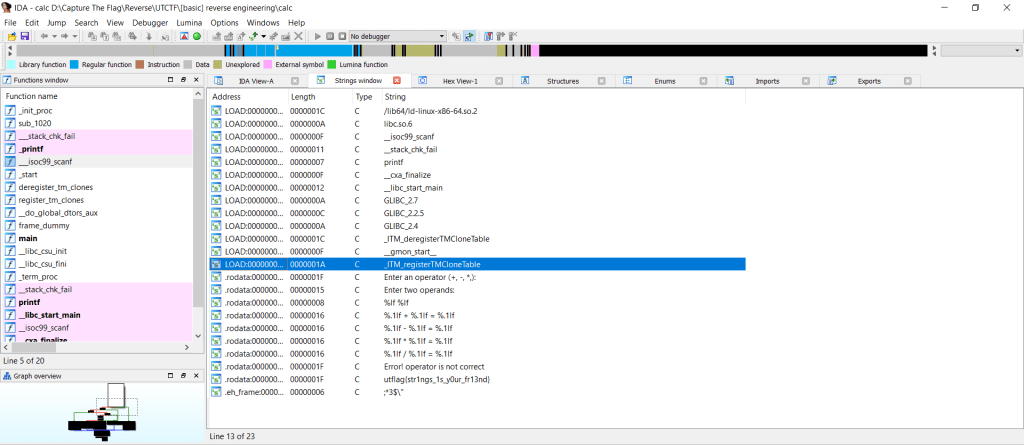
flag: utflag{str1ngs_1s_y0ur_fr13nd}
Challenge 2: babymips (50 pts)
Solution: I using Ghidra to see assembly easier 😉
XOR algorithm to get a flag
First i using exeinfoPE to view some information:
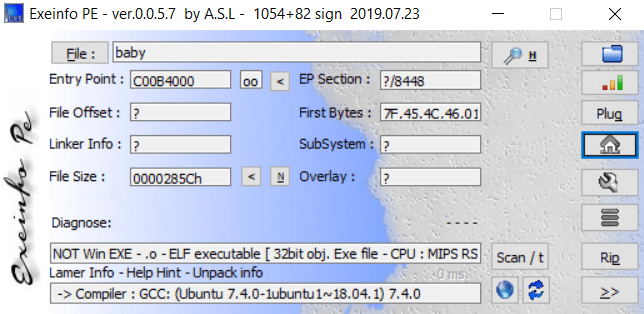
~ OK, a 32bit of ELF execuable file, now we strarting analysis main() function.
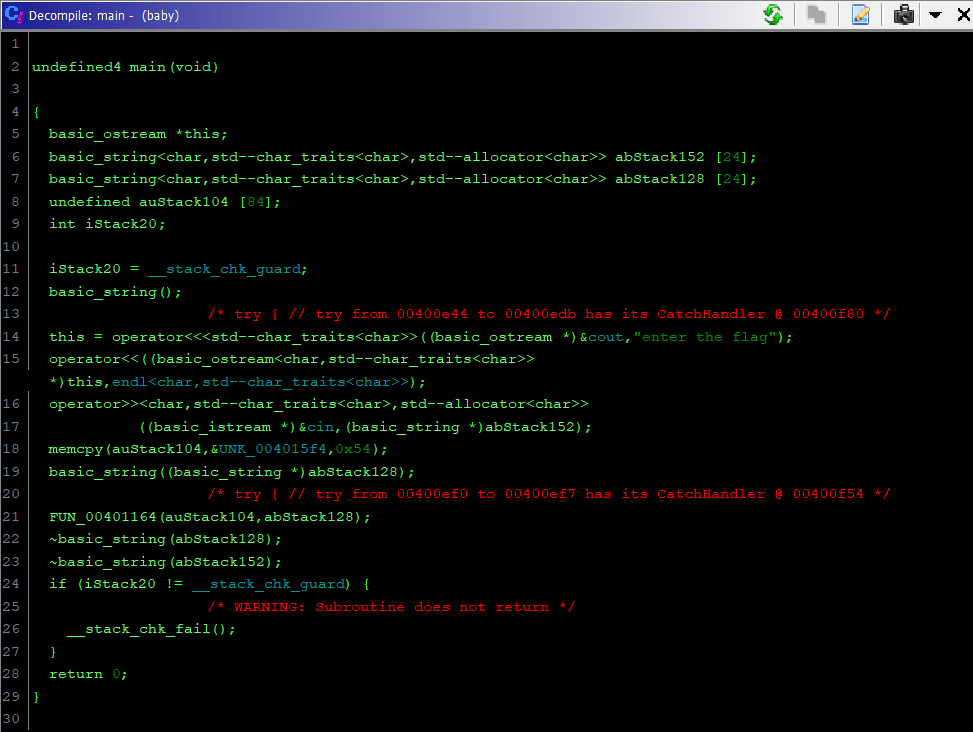
OK !!!, i have a maximum characters is 84 from memcpy command and i get an encrypted flag UNK_004015f4 but i don’t know the real length flag so i continue follow funciton FUN_00401164 in line 21:
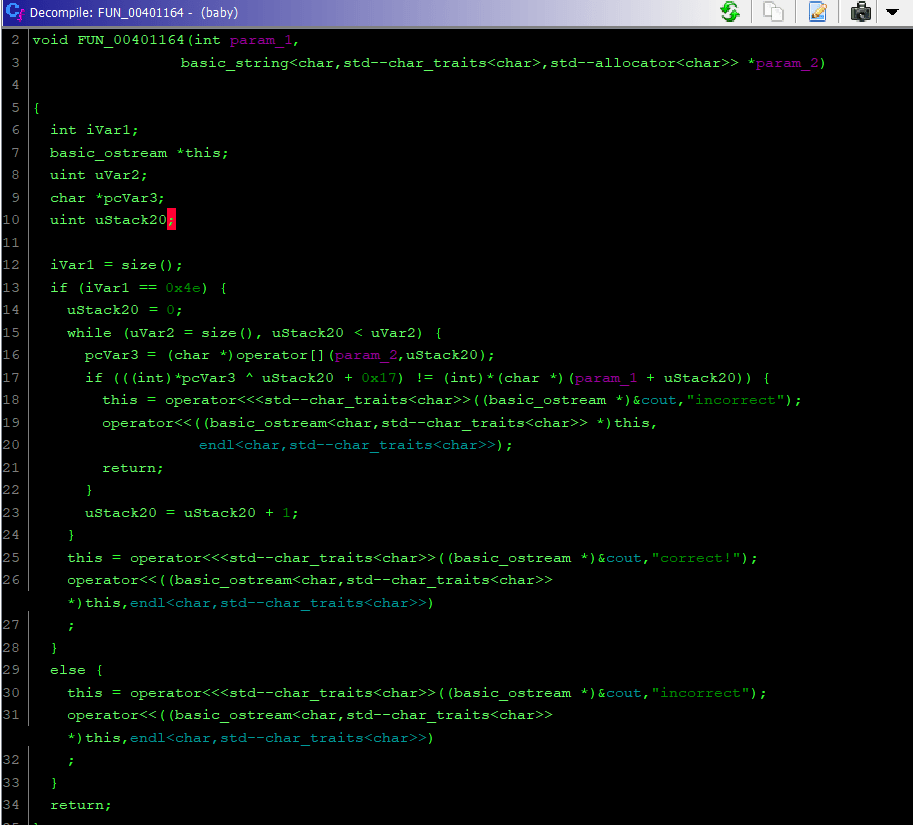
ARGIHT !!!, we can see in line 13: if(iVar1 == 0x4e), so we know the length of flag is 78 (0x4e) and bonus an encrypted flag in main() we have: 0x62, 0x6c, 0x7f, 0x76, 0x7a, 0x7b, 0x66, 0x73, 0x76, 0x50, 0x52, 0x7d,0x40, 0x54, 0x55, 0x79, 0x40, 0x49, 0x47, 0x4d, 0x74, 0x19, 0x7b, 0x6a,0x42, 0xa, 0x4f, 0x52, 0x7d, 0x69, 0x4f, 0x53, 0xc,0x64, 0x10, 0xf,0x1e, 0x4a, 0x67, 0x3, 0x7c, 0x67, 0x2, 0x6a, 0x31, 0x67, 0x61, 0x37,0x7a, 0x62, 0x2c, 0x2c, 0xf, 0x6e, 0x17, 0, 0x16, 0xf, 0x16, 0xa, 0x6d,0x62, 0x73, 0x25, 0x39, 0x76, 0x2e, 0x1c, 0x63, 0x78, 0x2b, 0x74, 0x32,0x16, 0x20, 0x22, 0x44, 0x19
Continue in line 17: a simple XOR so we can get a flag by python:
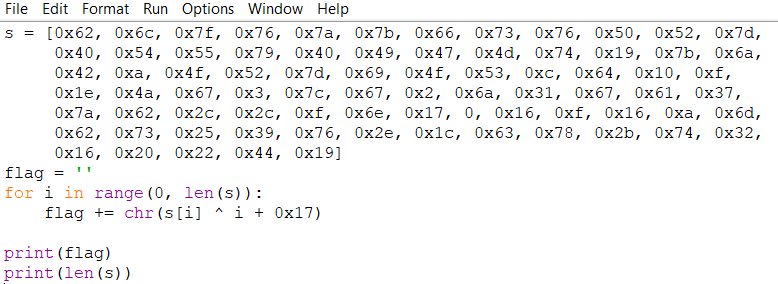
🙂 Finally we got the flag: utflag{mips_cpp_gang_5VDm:~`N]ze;)5%vZ=C'C(r#$q=efD"ZNY_GX>6&sn.wF8$vmvA@'}
Challenge 3: Crack The Heart (1411 pts) 🙂
Solution: using Debugger skill 🙂
~~ i spend 2 days to solve it 😦 ~~
Lucky this file is ELF 64 bit execuable !!!
Because this challenge is too long so i can tell you some ways to get a flag:
– First you must debug it so view this asm code !!
– after debug you’ll see a simple anti-debug so you must bypass it to see more asm code
– set breakpoint your input and get all values in bl registers and al registers, expect bl you must trace 1 loop to see the next value on bl registers, all the values of al, bl you can see it in command xor bl, al
– you can find values of al registers in address 0x402137
*note: you just see asm code while debugging 😉
after that you can get a flag by using python:
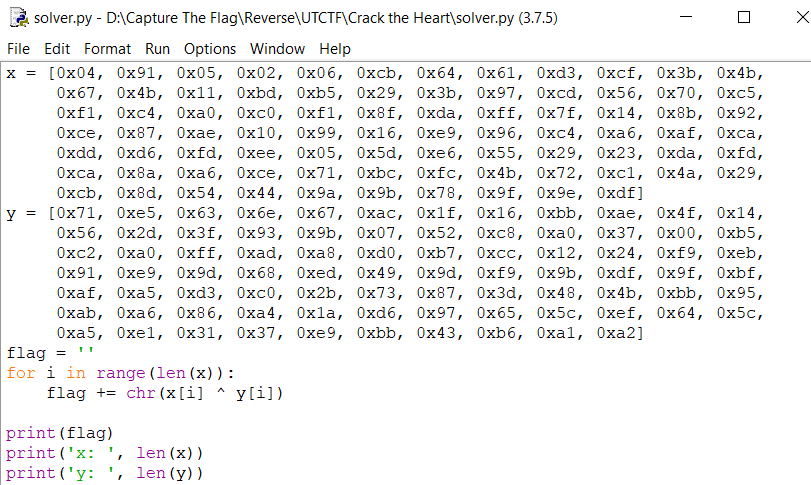
flag: utflag{what_1f….i_mapp3d_mY_m3m0ry_n3xt_to_y0urs….ahahaha, jkjk….unless ;)?}
i know somebody didn’t understand what i said so you can contact me in telegram: t.me/Th3Sea001
Anyway, this challenge reversing so interesting, thank you UTCTF ❤