link challenge: http://ctf.batamlinux.com/challenges#Tic%20Tac%20Toe (Reverse Engineering)
First i need information of tictactoe so i used exeinfoPE
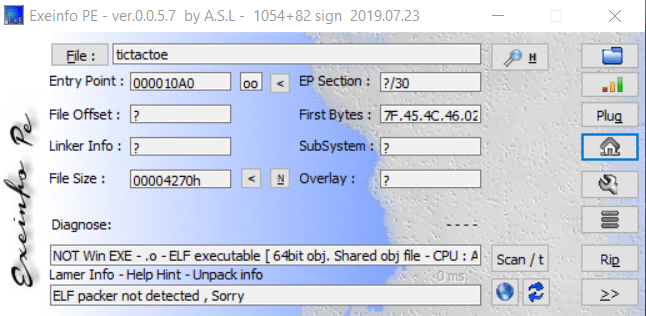
Solution: I found a “big” bug in this file could be shown a flag without playing a minigame :). It’s true ?, YES !!!, a flag contained in function mem(), now I’ll analysis all function in TicTacToe
Main()
TicTacToe is a carogame (3×3) has 2 players, if player 1 or 2 write 3 X (O) continuity, they’ll win, so in func main() i decompile it to analyse:
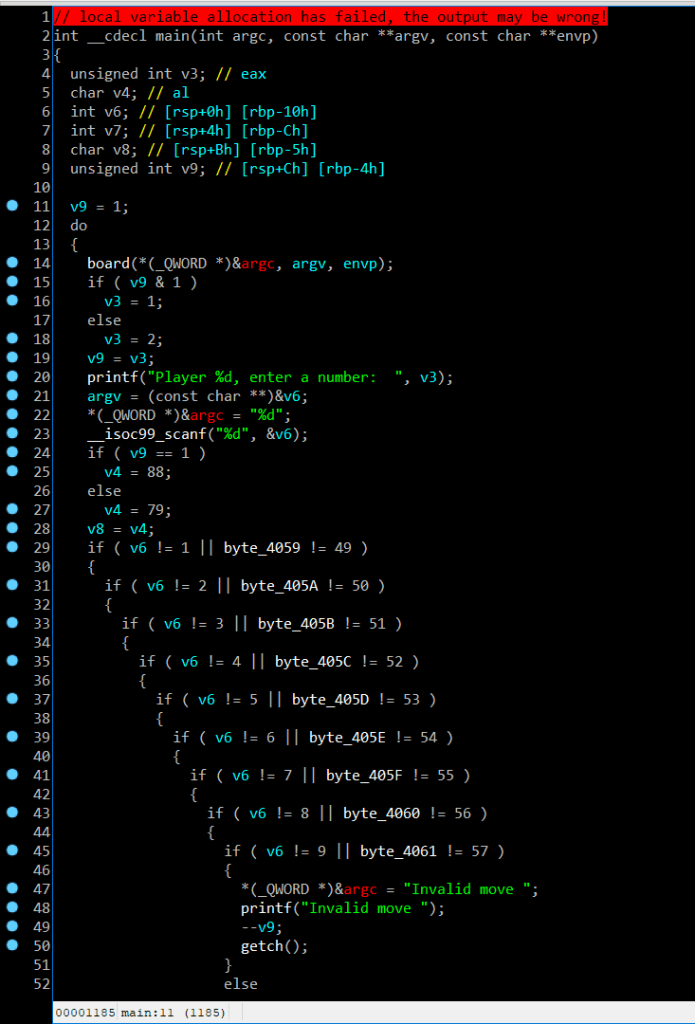
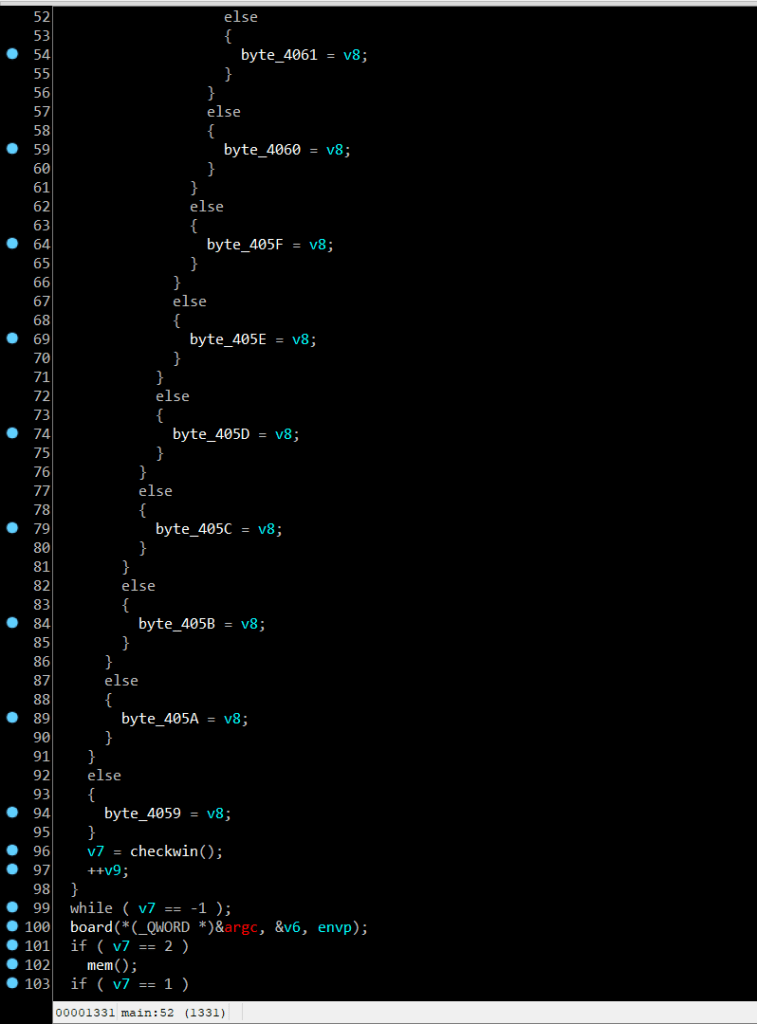
In line 29 ->45 are checked if correct move, go to func checkwin() and if right, it’ll be return 2 and unless, it’ll return 1. So mem() function is contain a flag, but unfortunally this file cannot run without file libncurses.so.6,…..so sad but that’s OK, let’s analysis this func !!!
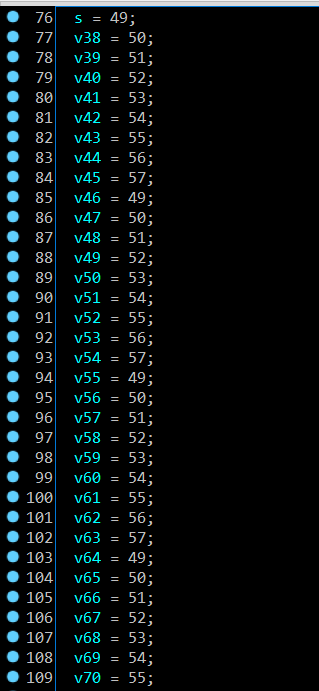
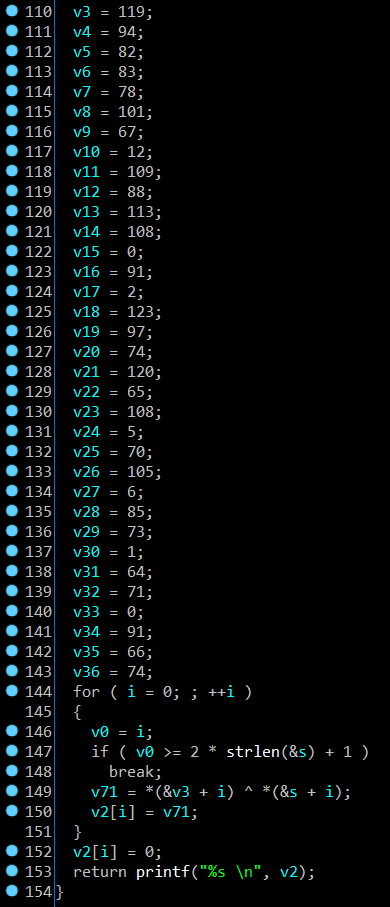
Here we are, an encrypted flag with using XOR algorithm in line 149, did you think a length password is 68 (from s to v70) ?. No, that’s not right because you saw line 149, there was v3 variable xor s variable. It mean divided into 2 parts: v3 (v3 –> v36) and s (s –> v70), when i checked length, the answer is 34 and did you see some number in array S (i called it) is 49, 50, 51, 52,…57 and continue loop ? This is a big problem which i want to tell you, let me describe it: when you use loop while used xor algorithm, (49 + i) will be ascended to 57, if (49 + i) or you can understand (&s + i) > 57, it’ll return back.To more describle it, i’ll code by python:

after you run this, you’ll get the flag 🙂
anyway, this challenge so interesting, i spent much time to solve it. Maybe i’ll stop this writeup, if you don’t understand about this challenge, here is my telegram: https://t.me/Th3Sea001
—————— THANKS FOR WATCHING ——————–