Challenge: [What’s the Password: Revisited] (Reverse Engineering)
Author: DarkEnigma
First, I drop the file into exeinfoPE to see some information
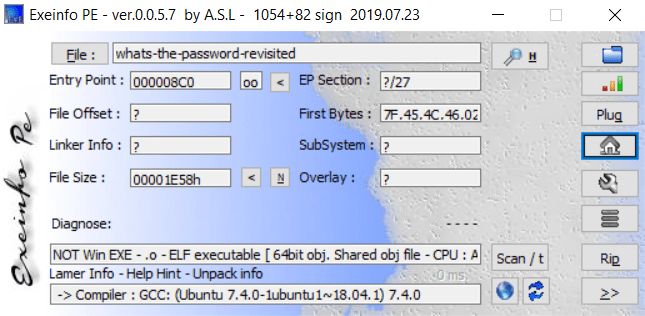
And you can see it’s an ELF64 for x86-64 structures, now i’ll analyse it by using IDA Pro and decomplie it from funcion Main.
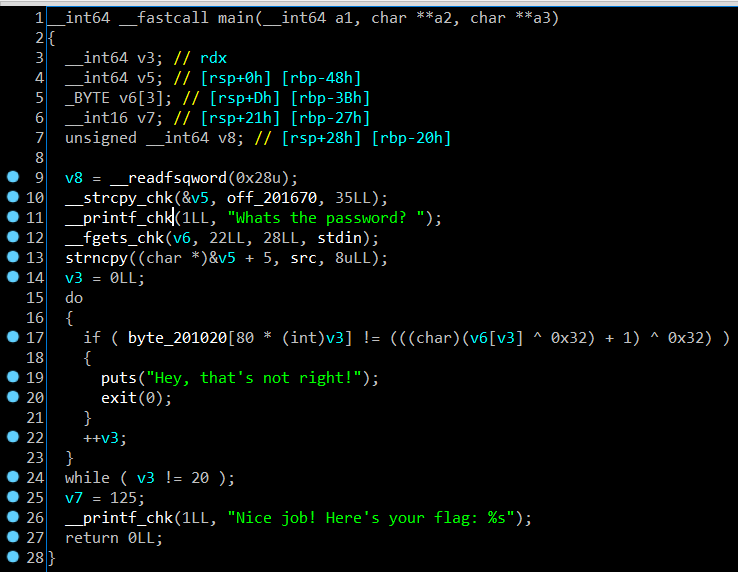
OK, i saw loop at line 15 to 24, you’ll see a conditional v3 != 20 it mean the length of password, so I started at line 10 and see off_201670 in a strcpy command, the off_201670 is returned result “rtcp{” and store in v5 variable . Then, in line 13 i see strncpy((char *)&v5 + 5, src, 8uLL), it mean it’ll copied v5 and src has 8 characters, the src i found it in IDA at address 0x201668 and 0x201670
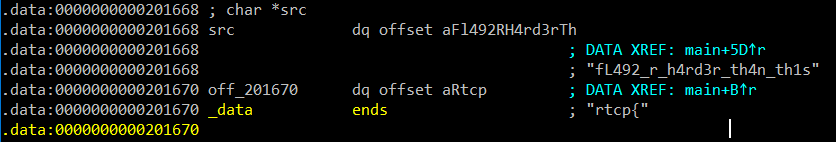
So, i easy found the flag from the scrncpy command which is: “rtcp{fL492_r_” :), next i continue to see conditional at line 17:
v3 = 0LL;
do
{
if ( byte_201020[80 * (int)v3] != (((char)(v6[v3] ^ 0x32) + 1) ^ 0x32))
{
puts("Hey, that's not right!");
exit(0);
}
++v3;
}
while ( v3 != 20 );
This conditional has algorithm XOR and i see byte_201020 elements at 0x201020
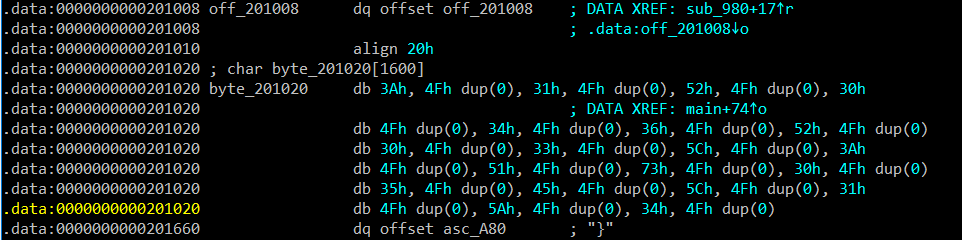
You can see the elements with the max size is 0x4F so i collects value: 0x3A, 0x31, 0x52, 0x30, 0x34, 0x36, 0x52, 0x30, 0x33, 0x5C, 0x3A, 0x51, 0x73, 0x30, 0x35, 0x45, 0x5C, 0x31, 0x5A, 0x34 and i coded it by python

After run it, we have the flag: rtcp{fL492_r_50m371m32_5Pr34D_0U7}
——————————– THANKS FOR WATCHING ——————————–
